The Logic of Access
Identity infrastructure that answers to you, not external services.
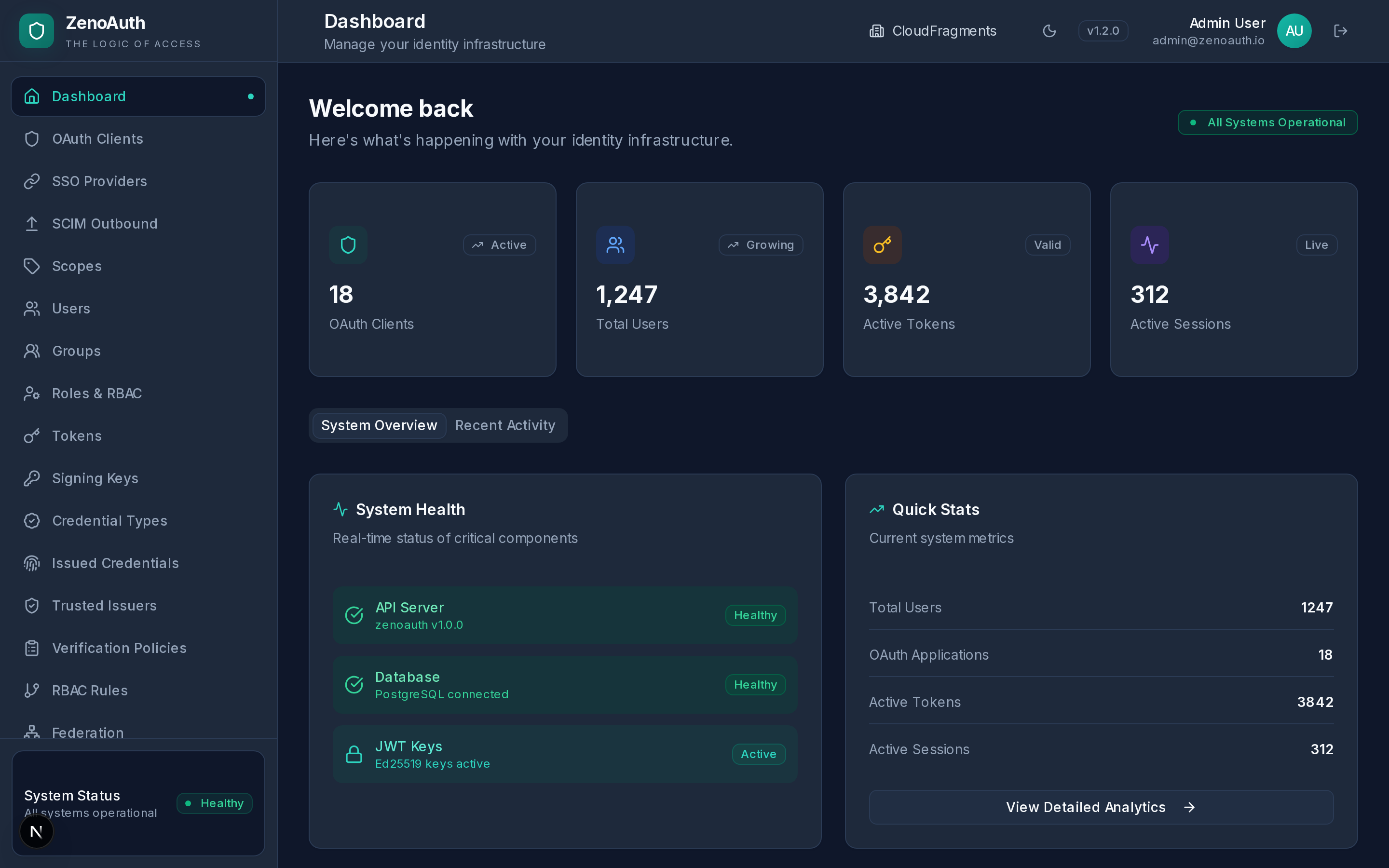
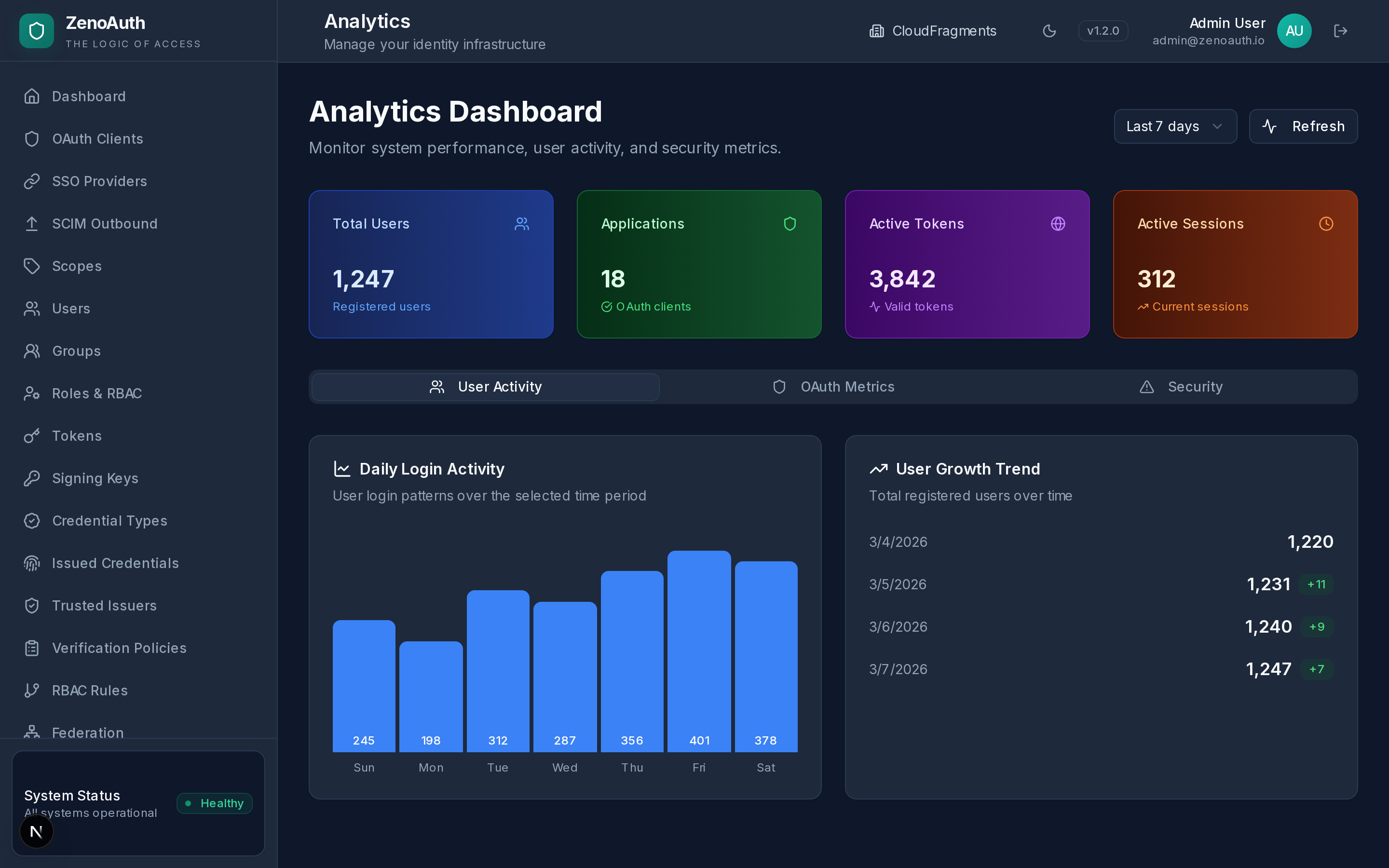
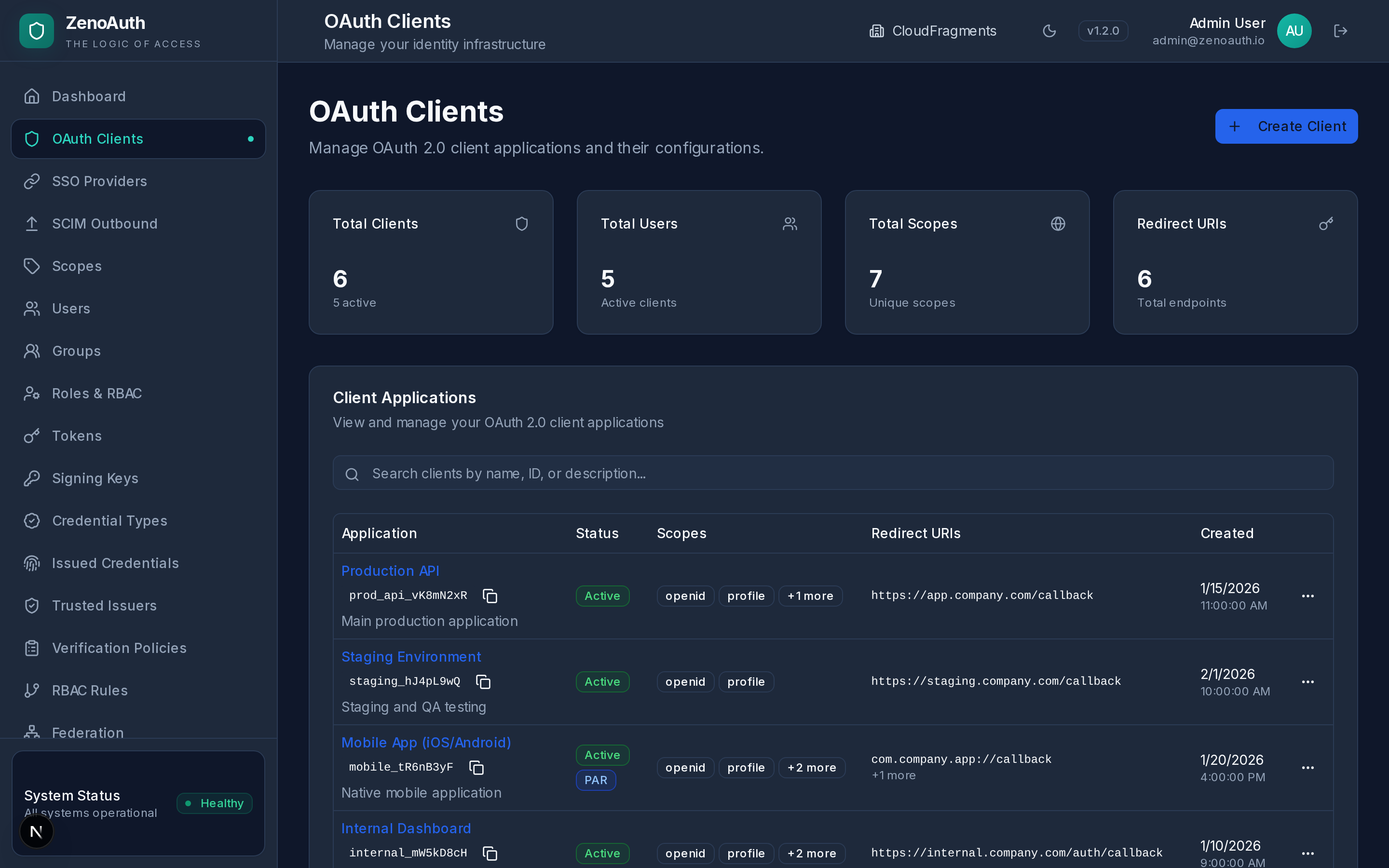
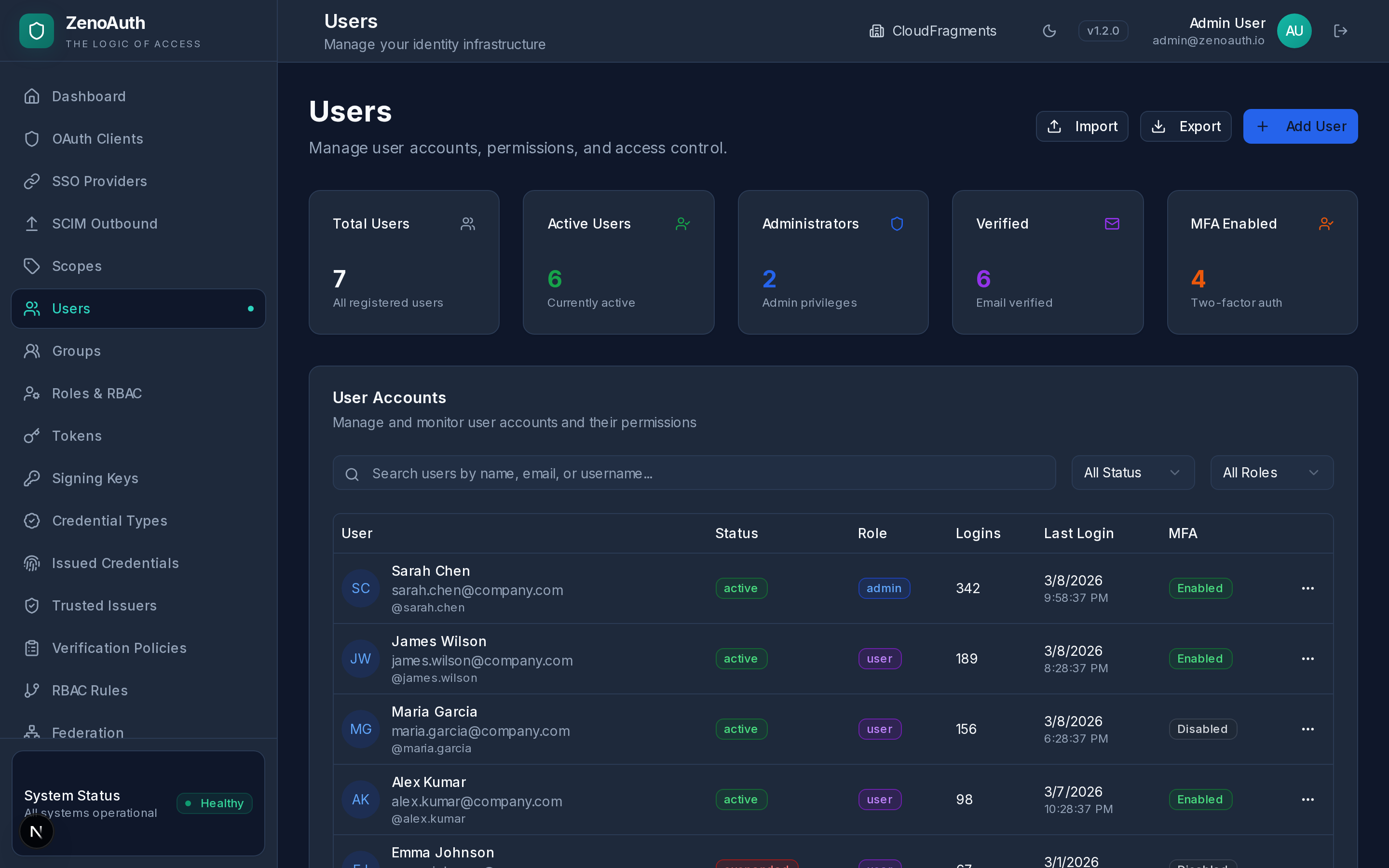
Your authentication layer is the one thing you cannot afford to get wrong. ZenoAuth puts it under your direct control — a single 11 MB binary, one PostgreSQL database, nothing else. Built in Rust for memory safety without garbage collection pauses.
Cloud from €20/month (planned 2026) · Self-hosted €5,000/year